AI-Aware Repository Guardrails
Cryptographic protections for sensitive code when using AI coding assistants. Lock critical files, enforce approval workflows, and maintain tamper-evident audit trails - entirely local, no backend required.
- id: core-configs
match:
- package.json
- package-lock.json
- tsconfig.json
approvals_required: 1
"ts": "2025-10-06T18:14:07.418Z", "action": "edit_reverted", "actor": "Bewaker Dev <hello@bewaker.ai>", "files": ["config/environments/prod/api.yaml"], "reason": "attempt:4 | policy:core-configs", "prevHash": "ba3a9f8e1b1c5d1f…", "hash": "4f5d0d441d54c4b4…"
What Bewaker locks down
Comprehensive protection for your most sensitive code and credentials
Policy-driven guardrails
Define .guardpolicy.yml rules to lock specific files, directories, or patterns. Enforce cryptographic integrity and restrict what contributors — including AI tools — can modify.
Line-level locks
Apply granular protection down to individual lines. Prevent drift, overwrites, or unapproved edits in sensitive regions (like secrets, configs, or business logic).
Tamper-evident audit chain
Every lock, unlock, and verification event is chained using Merkle roots and Ed25519 signatures, creating an immutable local audit log.
AI session tracking & unlock approvals
Detect when AI-assisted edits occur, automatically elevate guard policies, and require explicit unlock approval before protected code can be changed.
How it works
Four simple steps to cryptographically enforced security
Define guard policy
Create a .guardpolicy.yml file that specifies which files, directories, or patterns to protect — and what level of approval or oversight is required.
Lock repository
The Bewaker extension generates a cryptographic lockfile (.guardlock) containing Merkle tree hashes and Ed25519 signatures for all protected resources.
Enforce in editor & git hooks
VS Code surfaces guardrails directly in the editor. Pre-commit and pre-push hooks verify integrity and block unauthorized or AI-assisted changes before they reach your repo.
Verify & audit
Bewaker continuously validates locked content and records every lock, unlock, and verification event in a tamper-evident audit log — providing a cryptographic trail for compliance and forensics.
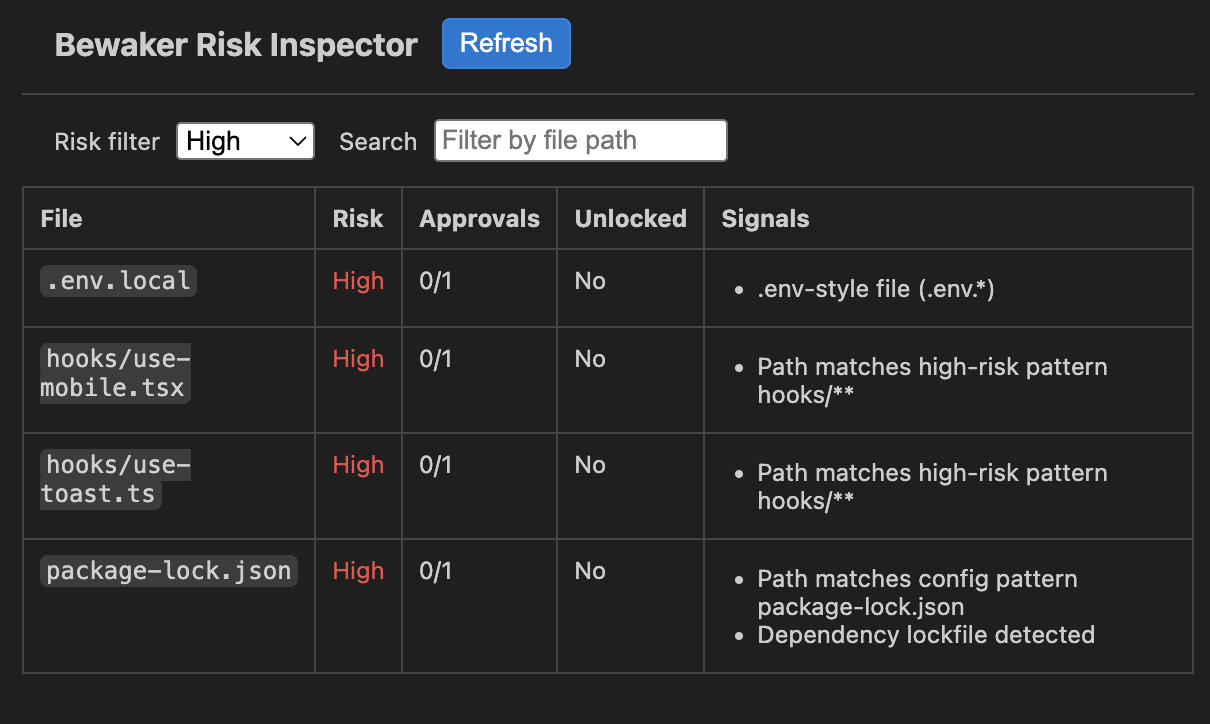
Heuristic risk visibility in real time
Bewaker’s Risk Inspector highlights files and code regions that carry elevated modification risk — from policy-protected files to patterns you define. See live context in VS Code as you work.
Policy-aware risk mapping
Surfaces protected and high-impact files directly in your editor.
Adaptive heuristics
Evaluates code structure and change patterns to infer relative risk levels.
Integrated experience
Color-coded indicators and a dedicated VS Code panel keep risk awareness inline with your workflow.
Local-first security
Your keys, your data, your control. No backend required.
Local key storage
Ed25519 keys never leave your machine
Offline operation
Works without internet connectivity
No telemetry
Zero data collection or tracking
Apache-2.0 license
Open source and freely auditable
Why engineers pick Bewaker
Early access teams are shaping the next generation of AI-safe development.
Want to be among the first voices here?
Join the WaitlistGit hooks & CI integrations
Enforce guardrails at every stage of your development workflow
Pre-commit enforcement
Verify protected files before a commit is allowed.
Pre-push validation
Double-check integrity before code leaves your machine.
Optional CI verification
Run the same integrity checks in your pipeline or a server-side pre-receive hook to keep repos provably intact.
Install Git hooks (no CLI):
Open VS Code → Command Palette → “Bewaker: Install Git Hooks”.
Pricing
Start free with open source. Scale with Team Edition when you need enterprise features.
Open Source
Full cryptographic protection for individual developers and small teams
- Unlimited guard policies
- Local-first architecture
- Git hooks integration
- Risk Inspector UI
- Tamper-evident audit logs
- VS Code extension
- Local key storage
- Community support
Team Edition
Enterprise-grade features for organizations scaling AI-assisted development
- M-of-N approval workflows
- SSO integrations (SAML, OIDC)
- Centralized policy management
- Team audit dashboards
- Priority support
- Air-gapped deployment
- Adaptive risk heuristicsML-ready
- Compliance lensesRoadmap